Crossplane - composing cloud infrastructure in a more effective way
Contributor: Rodion Slepnev
Crossplane is an open-source software operating as an add-on on top of Kubernetes letting to provision infrastructure of any complexity and configuration using most prominent cloud providers such as Google Cloud Platform (GCP), Microsoft Azure and Amazon Web Services (AWS) as well as other like Equinix, Alibaba Cloud and Red Hat Cloud Suite and operates across Mac, Linux and Windows operating systems. Being an extension of Kubernetes it runs on Google Kubernetes Engine (GKE), Azure Kubernetes Service (AKS), Alibaba Container Service for Kubernetes (ACK), Amazon Elastic Kubernetes Service (EKS) and others.
It enables to describe infrastructure declaratively without writing any code and extensively disclosing the underlying infrastructure of the particular vendor.
Crossplane extends Kubernetes cluster, providing ready-to-use Custom Resource Definitions (CRDs), which create a new custom resources with a name and schema that are specified by a user. It is also possible to compose these granular resources into higher level abstractions that can be versioned, managed, deployed and consumed.
Figure 1 represents an example of composed infrastructure implemented via Crossplane making possible to combine resources from different vendors.
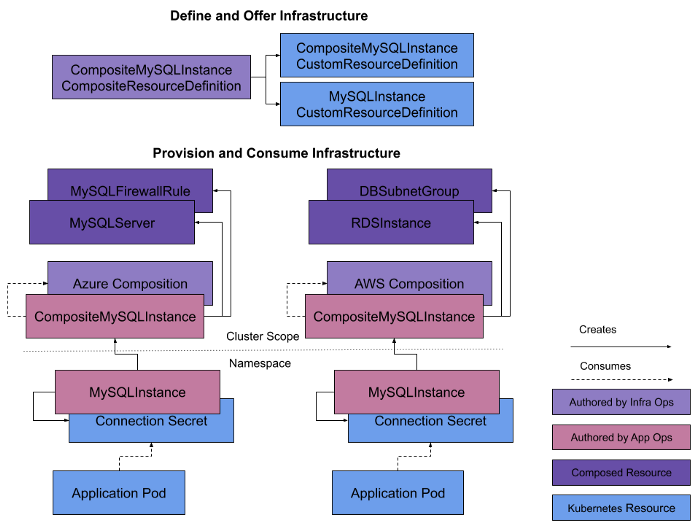
Furthermore one can build his own internal infrastructure abstractions on top of the CRDs from Crossplane. New custom APIs can include policy guardrails, hiding infrastructure complexity — set of CRDs and controllers are bundled together known as packages that represent and manage external infrastructure (i.e. a provider), then installing them into a cluster where Crossplane is running.
Installation process:
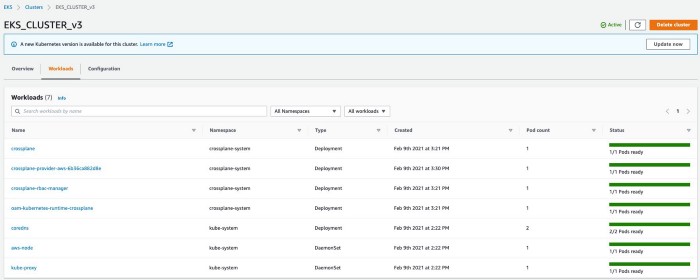
Following the guidelines we installed Crossplane on AWS EKS although. Figure 2 shows what applications are being launched on the cluster (so-called workloads).
Example as proof of concept:
Figure 3 shows the custom script composed from two CRDs which creates a VPC with a Security Group in AWS environment (all default examples could be found here).
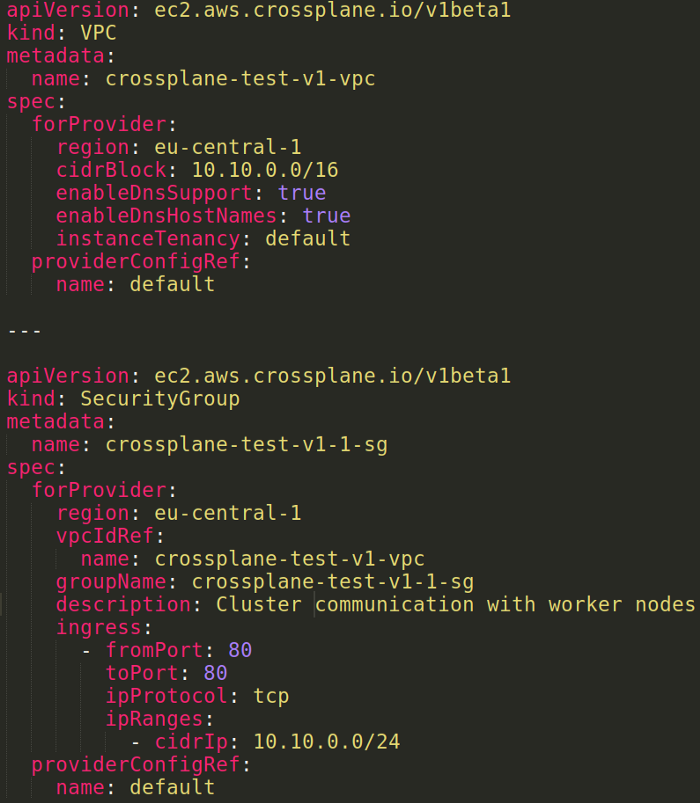
The script itself describes infrastructure declaratively which as mentioned above lets encapsulate its specific details by using predefined words without writing any code and/or implementing it via internal sources like, for example, AWS Cloudformation.
Descriptions of CRDs provided by Crossplane for all versions together with the references to the corresponding branches on GitHub can be found here.
Script is being implemented via kubectl (Fig.4) as it is also mentioned with examples in the guidelines:
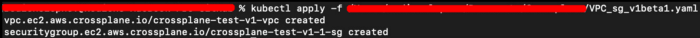
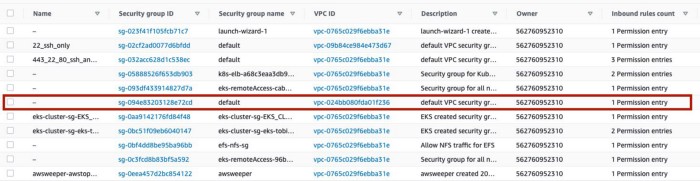
As a result one can see successfully provisioned Virtual Private Cloud (VPC) with a dedicated security group (Fig.5 and Fig.6):

Conclusion:
Crossplane is currently under active development with a small community but showing reasonable progress looking at fixed issues. Although it has bugs being not fixed yet, features that are not reflected in the documentation especially installation part and the final stage is still far from completion Crossplane shows a quite good potential and in perspective could become more popular tool in its application area like, for example, Pulumi and other tools with similar functionality.
Thinkport is an actively developing company trying to find new approaches and technologies that concern cloud computing and relevant topics and it was very exciting to find and research Crossplane in one of its projects where it takes an active part. If you have further specific questions on the topic, or a handful of niche areas we are specialized in, visit our newly updated workshop page.
References:
1. Crossplane official website — https://crossplane.io
2. Crossplane GitHub repository — https://github.com/crossplane
3. Crossplane documentation — https://crossplane.io/docs/v1.1
4. Kubernetes documentation — https://kubernetes.io/docs/home
5. CRD descriptions — https://doc.crds.dev/github.com/crossplane/crossplane
Blog Kurator






